This paper presents an evaluation of the. Fraudsters use a variety of techniques to acquire a victims card number.
If an identity theft suspect has been arrested request.

. See our ID Protection Reviews Find Who Is Rated 1. Ad Think You May Have Been Targeted by Identity Theft. Ad Credit Monitoring Can Help You Detect Possible Identity Fraud Sooner And Prevent Surprises.
This training course is designed to provide an overview of identity theft and trends as well as a look at investigation techniques in identity theft cases and crimes. Compare Identity Theft Protection Reviews. Identity theft since it may occur only once and be discovered quickly by the credit card issuing company often before even the individual card holder knows it.
Online ID theft techniques investigation and response 77. Speak with a Specialist Today. Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise.
Get the Tips and Guidance You Can Trust Free of Judgment. Examples of how stolen personal information can be used to. It can happen to anyonebut there are steps you can take to protect yourself and to recover if it happens to.
Mining of Intrusion Detection Systems. Fraudsters side and the first level of this investigati on process analysis was hence presented. Other types of identity theft.
Identity theft occurs when someone uses your identity in a crime or fraudulent act. How To Protect Your Identity Today. The threat of identity theft is on the rise.
These techniques are listed under three headings. Online organisations commonly use electronic commerce approaches. The process of investigating cybercrimes includes.
Some of the ways include using high-tech devices known as skimmers to swipe the card so as to collect the. Introduction and Background CIPPIC Working Paper No1 ID Theft Series March 2007 Ottawa. Choose Your Plan Today to Stay Safe.
First file the theft with the Federal Trade Commission FTC and receive an identity theft affidavit which you will then take when you file the crime with the local police and get a police report. Appendix I contains a more detailed description of our audit objective scope and methodology. However these have some limitations in the m-commerce.
The ID Theft investigation framework disti nguishes the examination in the victims and the. Free Monitoring Of Your Experian Credit Report With Alerts When Key Changes Occur. Compare Identity Theft Protection Reviews.
CIPPIC 2007 Identity Theft. See our ID Protection Reviews Find Who Is Rated 1. All Major Categories Covered.
E xamining identity theft suspects requires systematic methodical techniques designed to yield evidence for possible prosecution. 2 Identity theft has swiftly become a serious issue for victims police and prosecutors and is a. As technology advances so do the techniques used by identity thieves.
Join Today to Protect Your Credit Card Passwords More. Ad Best Identity Theft Protection Services 2022. And 3 social engineering.
The University of Glamorgan and is currently working towards a PhD in Data. Taking a citizen complaint Locating the IP address of the suspect Gaining access to the IP address of the Internet service provider. Dont Wait for It to Happen.
Ad Best Identity Theft Protection Services 2022. Online ID theft techniques investigation and response 77. Ad Discover the Best Identity Theft Security Services.
Related to identity theft investigations prosecutions personnel resources and victims. How To Protect Your Identity Today. Canadian Internet Policy and Public Interest Clinic.

Identity Theft Investigations Pinow Com

Pdf Identity Theft Identity Fraud And Or Identity Related Crime

Calameo Identity Theft Protect Your Identity Online

Pdf Online Id Theft Techniques Investigation And Response

Tips And Advice To Prevent Identity Theft Happening To You Europol
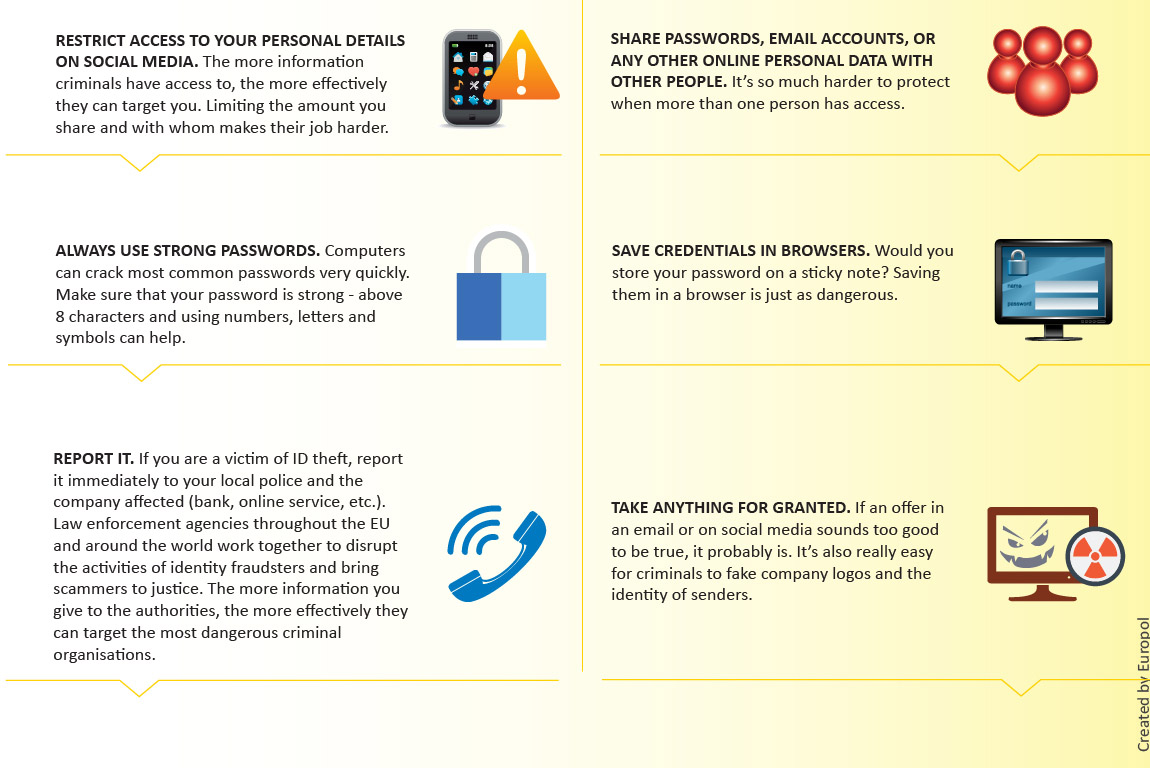
Tips And Advice To Prevent Identity Theft Happening To You Europol


0 comments
Post a Comment